Across the world the majority of computer users are still using Windows 7 operating system, and Windows 8, Windows recently announced the update of the version of Windows 8, the Windows 8.1 operating system. Although only minor changes, but Microsoft presents Windows 8.1 with new features to complement the previous version.
Microsoft seems to be really heard many complaints about the way the interaction with its predecessor, Windows 8. It is seen with a variety of changes to the operating system (OS) is the latest Microsoft. The changes really just minor, but these changes seem to be able to restore a sense of comfort that had disappeared in the use of Windows 8.
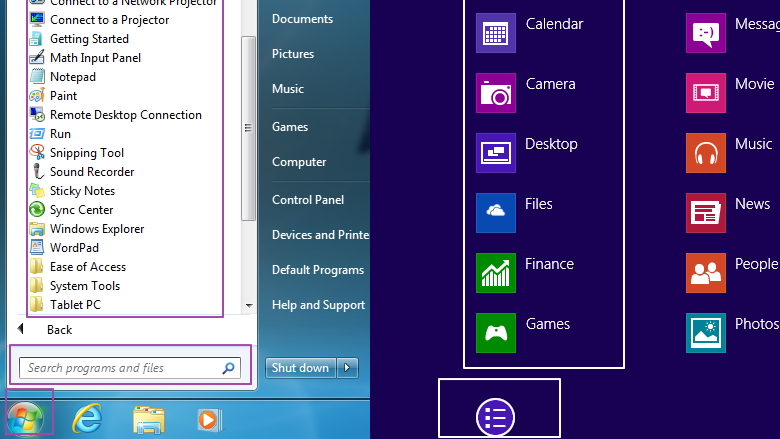
Probably one of the most anticipated changes is the Start button. Yes, Microsoft finally return the keys that had disappeared from Windows 8. The "new" is actually just a metro-style Start screen displays when it is clicked. If desired, the user can make the Start Screen display the "all apps" to restore the workings of the traditional Start button.
Users can also right-click on the Start button to see some of the other menus, such as Task Manager, Control Panel, Search, and Run. In fact, the user can turn off the PC via the Shut Down menu directly through the menu.
Users can also set the Start screen and the desktop using the same wallpaper. This feature makes the user will not be too confused if you want to move from the desktop to the Start Screen.

Screen lock screen did not escape the changes. Now users can install photo slideshow, receive Skype calls, and access the camera directly from the screen.
Although only minor changes, but Microsoft presents Windows 8.1 with new features to complement the previous version. In an event that was held some time ago in San Francisco, United States, users can download the final version of Windows 8.1 by year-end through the Windows App Store, while who can not wait can already taste it through the Microsoft website.
Overall there are a lot of new features offered by the software giant, but Microsoft is more menintikberatkan the capabilities desired by the user.
Start menu Windows 8.1 coming back
Well, of dozens of new features in Windows 8.1, there are several features that are considered important by users, the following 12 new features in Windows 8.1:
- Automatic Update Application. Applications that you download from the App Store now Microsoft will update itself every time the developer released a new version. Later origin connected to the Internet, users will no longer find the update notification icon of the application that is embedded in the Windows App Store. However, there is some confusion what would happen if the renewal application requires more permissions like access to the site or contact list. A spokesman for Microsoft said that it will automatically update as well, even though it may violate some privacy rules Microsoft.
- The return of the Start button. Having previously eliminated Microsoft on Windows 8, the Start button is now re-presented in the Windows 8.1 version. Features is quite small, but this is quite helpful. The button will take the user to the main page of Windows 8. Also, the Start button will give you access power user command to turn off or turn on the device again.
- 4 Running Applications Simultaneously. Window in Windows 8.1 now allows you to work with up to four apps on one screen through Snap.Tapi features does this depends on the screen size of the device you are using. For example, if the user is using a large screen such as a notebook, then let you run 4 of each application on each screen. However, the smaller the range tablet 8 inch will still restrict you to open two windows.
- Mode 'Hands-free'. Updates are not less attractive in Windows 8.1 is a mode called 'hands-free'. Users can scroll through web pages were read without touching it. This mode will be connected to the camera screen is usually printed on the tablet or laptop. So when you waved a hand in front of the screen, then read the article will move.
- Opening Camera While Locked. Microsoft added some new features that better matched for small sized tablet embedded with Windows 8.1. Later, the user can use the camera without opening the tablet. Small features that have great functionality for penggunananya. Also, Microsoft added some new moves for the screen keyboard to make typing on a smaller screen easier.
- More updates home page. New customization in Windows 8.1 lets you choose a desktop background color more and more diverse. It also lets you change the size Tiles.Pengguna can also change the look to a classic Windows 7 interface. It can be temporary with a set period of time. Personalize in customization allows users to some background Tiles with interesting pictures.
- Alternative Miracast Bluetooth. Miracast is an alternative to Bluetooth that offers high-speed wireless connections to other devices. It can connect the projector to a Windows 8.1, Xbox One, other gaming consoles wirelessly to a TV or other device supports Miracast over, too. This is great for streaming video or playing a game of small tablets to larger, such as a TV.
- Booting to Classic Mode. As we all know, Windows 8 offers a frontal changes, including in terms of the interface. Unfortunately, not all the fashion boxes like those operating systems. After a lot of feedback from customers who ask for it, Microsoft is finally allowing users to boot the computer to the classic desktop mode instead of Windows 8 menu. To activate this mode, the user will be able to perform a number of settings through the settings in the settings.
- New Search technology. Windows 8.1 using Microsoft's Bing search technology. As with previous versions, users can find the search bar on the right side of the screen. Instead of looking for files or applications in the form of a category, Windows 8.1 allows the possibility to look up anything on the computer or the Web in a single step. Leblond, Head of Windows Program Management said, "We think this will really change the way you interact with the web and with Windows making it quicker and easier to get something diinginkan.Ini is a modern version of the command line. Results from a local file, applications and settings are easily accessible in the same cozy look by rolling to the left.
- Get connected to SkyDrive. To store photos, files and important documents, Windows 8.1 provides a connection to Microsoft's online storage system, SkyDrive. Files can be stored directly, and even when offline, SkyDrive application will get the new update after files are made available to users.
- Using the Web Browser Internet Explorer 11. Latest OS will be available to use Internet Explorer 11. With a better performance than the current, users can load pages faster and some other new features. Leblond give an example that one can customize the look of modern IE11, to always display the address bar and have a lot of tabs open as you want.
- Have the Outlook application. Outlook email application present in Windows 8.1 for free with a lightweight version of Windows, called Windows RT made for tablets like the Microsoft Surface.
More complete all the new features in Windows 8.1 "Blue" build 9369 can be found in the following list:.

- Metro Applications
- New Alarms application.
- New Calculator application
- New Movie Moments application.
- New Sound Recorder application.
- New File Manager replaced Skydrive application.
- References to Windows Defender application.
- Updated Settings application.
- Automatic updates.
- User Interface
- Bigger/Smaller tiles for start screen.
- Slide up from start to view all apps screen.
- Slide to Shutdown feature.
- Color slider for theme.
- Slideshow for lock screen.
- Start screen sync.
- New search animation.
- Altered search panel.
- Multiple snapped applications on wide screen.
- Now apps can be snapped too on screen resolutions below 1366 x 768.
- Half-Half option for metro applications.
- Metro applications on multiple monitors.
- Thinner borders for some desktop applications.
- No transparent window on minimizing/closing.
- Support for touchpad gestures without any additional driver.
- Start screen group naming can be done without zooming out.
- Switching apps now lets you decide to put on left or right snap.
- Button on bottom of start page to enter app list.
- Search bar on the app list page.
- New animation for opening apps.
- Save on SkyDrive by default option.
- New device depending start screen icons.
- Access camera from lock screen by sliding down.
- Internet Explorer
- Synced tabs feature.
- Download list feature on metro version.
- Useragentstring added "like Gecko" which Firefox uses.
- History wipe on desktop like the one in metro version.
- References to WebGL support.
- References to Spdy-protocol support.
- Metro styled F12 Developer Tools
- Kernel
- Less ram usage.
- References to Minkernel.
- References to BaseFS.
- References to 3G/4G tethering.
- References to barcode scanning.
- References to Spdy-protocol support.
- Support for wireless displays (In Settings app)
- Support for touchpad gestures (In Settings app)
- ReFS enabled for client. Not only server anymore.
- DirectPlay. New Windows Feature.
- (Resilient File System) Key features of the new file system (ReFS)
- Metadata integrity with checksums.
- Integrity streams providing optional user data integrity.
- Allocate on write transactional model for robust disk updates (also known as copy on write).
- Large volume, file and directory sizes.
- Storage pooling and virtualization makes file system creation and management easy.
- Data striping for performance (bandwidth can be managed) and redundancy for fault tolerance.
- Disk scrubbing for protection against latent disk errors
- Resiliency to corruptions with "salvage" for maximum volume availability in all cases.
- Shared storage pools across machines for additional failure tolerance and load balancing.
You are interested to try it out?
Please download it free at the following link:
Download Full Version Microsoft Windows 8.1
Product Key: NTTX3-RV7VB-T7X7F-WQYYY-9Y92F
English 32-bit (x86), file size = 2.8 Gb
English 64-bit (x64), file size = 3.8 Gb
For those of you who are interested in the other language versions please visit the Microsoft website:
Author : Yohanes Gitoyo.
Sources:
http://www.hariandialog.com/ , Kamis, 27 June 2013 10:43.
http://www.didno76.com/, Sabtu, 29 Juni 2013.
http://www.windows8kita.com/
Diposkan oleh Yohanes Gitoyo, S Pd. di 6/30/2013 12:45:0