
The network of cyber security experts are now looking at finding information on the Flame, a computer software program called dangerous because it can penetrate a variety of computer networks and much more difficult to find.
Flame findings are re-prove what is before it has many security analysts warned the virtual world, which is that many governments are using a malicious computer program as a weapon for intelligence activities for several years. "This is just one of the many cases that occur over time and as this was never publicly known," said Alexander Klimburg, cyber security expert at the Austrian Institute for International Affairs.

Flame or Skywiper worm is a sophisticated cyber weapons combined capabilities of a Virus, Worm, Spyware, Backdoor, Keyloger, Trojan which is integrated able to infiltrate the most advanced information technology security system without being detected! So it is not wrong if there are a variety of media who called Flame as viruses, worms, trojan. Kaspersky Lab as a party to investigate the activity of this Flame categorized as a "worm / worm" with the nickname "Worm.Win32.Flame". Bit Defender Flame vendors categorize as "Trojan.Flamer.A / B".
In this article Flame virus is sometimes written, sometimes a worm, or trojan according to the sources we quote, please be advised.

Here is an explanation of Akexander aka Aleks Gostev, head of Global Research and Analysis Team at Kaspersky Lab was quoted as saying www.securelist.com .
What exactly is Flame? What did he do?

Flame, also known as Flamer, sKyWIper, and Skywiper, is a modular computer malware discovered in 2012 that attacked computers running Microsoft Windows operating system. This program is used to target cyber espionage in the Middle East countries. The discovery was announced on May 28, 2012 by the National Iranian Maher Center Computer Emergency Response Team (CERT), Kaspersky Lab and Lab CrySyS. Budapest University of Technology and Economics. The latter is expressed in his report that "sKyWIper certainly the most advanced malware we encountered during our training, you could say, it is the most complex malware ever found.".
Flame Worm known to have been "in the wild" since February 2010, so it has to avoid detection by security software for more than two years when it was discovered; main component file name has been observed in December 2007. The fire may remain undetected for longer, but the researchers came across while researching "wiper" exploit.
Flame is a sophisticated attack toolkit, which is much more complex than Stuknet / Duqu. It is a composite: Backdoor, Trojan, and has features such as WORM, which allows it to replicate in the local network and removable media if so ordered by his master. Flame has features that enable it to double as a worm in a local network and on storage media such as flash if instructed by the controller.

Flame the way in. It was not immediately known. It is estimated this program is inserted through targeted attacks is still unknown methods.
When a system is infected, the Flame will perform some action such as intercepting the network traffic that entered, tap the display on the monitor, record voice conversations, intercepting keyboard (keyloger) and so on. The Flame operator can upload more modules to enhance its capabilities.
Flame as sophisticated as what?
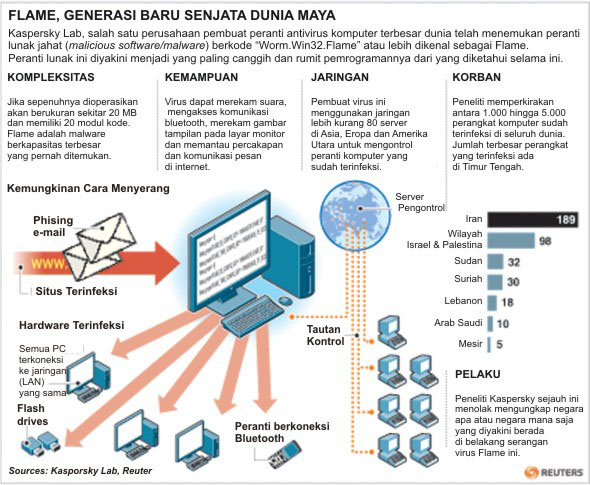
Flame consists of several modules that nearly 20 MB in size if it is fully uploaded. Because of its large size, he is very difficult to analyze. Flame large because it has many elements such as compression (zlib, libbz2, PPMD) and manipulation of database (sqlite3), including the virtual machine-based programming language Lua.
The virus has the code 20 times more than Stuxnet. Stuxnet itself is said to have made the production of uranium enrichment in Iran fails to function when attacked in 2010. This virus also has 100 times more code than the virus that is known is used to steal financial information.
Once infected systems, Flame begins a complex set of operations, including sniffing the network traffic, take screenshots, recording audio conversations, intercepting keyboard, and so on. All these data available to the operator via the link to the command-and-control server Flame.
Then, the operator can choose to upload more modules, which extend the functionality of Flame. There are about 20 modules in total and the goal of most of them are still being investigated.
Capability of recording data by Flame are also more complete as it can reach all forms of communication, whether audio, traffic data, display and use of keyboard tapping. Flame ability to spread itself via Bluetooth devices is also quite unique.

Recorded data is sent to C & C through a SSL channel secret, on a regular schedule. We are still analyzing this; more information will be available on our website soon ( http://www.kaspersky.com/ ).
This malware has the ability to regularly take a screenshot; anything else, it takes a screenshot when certain "interesting" the application is run, for example, IM. Screenshots are stored in compressed format and is regularly sent to the server C & C - such as audio recordings.
Flame consists of many different plug-ins - to 20 - who have a particular role is different. Certain infections with Flame may have one set of plugins seven, while other infections may be 15. It all depends on the type of information sought from the victim, and how long the system has been infected with Flame.
Officials at Symantec Corp. and McAfee security division Intel Corp., two leading antivirus manufacturer of the world, also is studying the Flame stated. "It seems far more complex, but it was too early to determine the scale," said Dave Marcus, director of research at one of McAfee.
Symantec Security Response Manager, Vikram Thakur, said experts at his company believes malware Flame is the most complicated system ever invented. Kaspersky research team said that the number of computers infected with this virus in most of Iran, followed by Israel and the Palestinian territories and Sudan and Syria.
Roel Schouwenberg, senior researcher at Kaspersky, called Flame and Stuxnet seems to infect the computer by way exploit security holes in Windows-based operating system. Both viruses also have similar ways to propagate themselves. "It could be the team that developed the Stuxnet have equal access to the technology used to make the Flame," said Schouwenberg.
When Virus Flame was created?

Worm Flamediidentifikasi in May 2012 by Kaspersky Lab, National Center for Iranian CERT Maher, and CrySyS Lab (Laboratory of Cryptography and Security Systems) from Budapest University of Technology and Economics as Kaspersky Lab was asked by the UN International Telecommunication Union to investigate reports of a virus that affects the Oil Ministry of Iran computer. As Kaspersky Lab investigated, they found an MD5 hash and file name that appears only on customers machines from Middle Eastern countries. After finding more pieces, the researchers dubbed the program "Flame" after the name of one of its modules.
According to Kaspersky, Flame has been in operation since at least February 2010. CrySyS reports that the file name of the main components have been observed in early December 2007. However, the date of manufacture can not be determined directly, since the date of manufacture for the wrong malware module is set to a date in early 1994.
The creator of Flame Virus specific change file creation date for each investigator could not determine the truth of creation again. This file is dated 1992, 1994, 1995 and so on, but it is clear that this is a false date.
Computer experts consider it the cause of the attack in April 2012 which led to the Iranians for their oil terminal disconnect from the Internet. At that time the Iranian Students News Agency called malware that caused the attack as a "wiper", a name given to him by the creators of malware. However, Kaspersky Lab believes Worm Flameyang possible "infection is completely separate" from malware wiper. Due to the size and complexity of the program-described as "twenty times" more complicated than Stuxnet-Lab states that a full analysis can require as long as ten years.
On May 28, Iran announced that CERT has developed a program of detection and removal tool for the Flame, and has been distributed to "select the organization" for several weeks.
We assume that the fire created a major project, not earlier than in 2010, but still has an active development today. Creators continue to introduce changes into different modules, while continuing to use the same architecture and the name of the file. A good number of modules made of changes in 2011 and 2012.
According to data from our own, we see the use of fire in August 2010. Moreover, based on collateral, we can be sure that the fire out in the wild in early February to March 2010. It is possible that before that there are no previous versions, but we do not have data to confirm this, but chances are very high.
What is the difference Flame with another virus? Is there a new one?

Virus-sized Flame 20 MB (if uploaded all), so it is difficult in the analysis. Flame is so big reason why is because it includes different libraries, such as for compression (zlib, libbz2, PPMD) and manipulation of the database (sqlite3), along with the Lua virtual machine. So far, the use of Lua in the malware can be spelled out very rare. Similarly, the large size of this virus. Generally, today's malware is small and written in a practical programming language so easily hidden. is uncommon. Method of concealment through the use of a very large program code is a novelty that brought Flame.
Lua is a scripting (programming) language, which can be easily extended and linked with C code Fire has a lot of high-order logic is written in Lua - with an effective attack and the subroutine library of C + + compiled. Effective part of Lua code rather small compared to the overall code. We estimate the 'cost' of development in Lua is more than 3000 lines of code, which for the average developer will take about a month to create and debug.
Also, there is a local database is used internally by the SQL query nested, multiple encryption methods, different compression algorithms use Windows Management Instrumentation scripting, batch scripting and more.
Flame virus runs automatically even when the system boots, it is also less likely for the detection of anti-virus because he was not a conventional executable application, but has a component of some DLL files are automatically loaded during system boot.
Overall, we can say Flame one of the most complex threats ever found.
Who is behind the Flame?

The findings of the latest computer virus Flame, which is feared to be malicious software or malicius software (malware) strongest ever sparked fresh concerns about a new round of cyber war. Some evidence suggests the virus is likely to be of the order of one or a number of countries that used to be responsible for the Stuxnet virus attacks in 2010 and then attack the Iranian nuclear program.
The researchers from Kaspersky Lab, the creator of the famous Russian antivirus program is the first time found evidence of infection Flame on a computer network is by far the state has not found evidence of what works similar like Stuxnet Flame. They also refused to reveal which country is responsible in tow.

When the first Stuxnet attack, Iran accused the U.S. and Israel as a charge.
So far there are three parties usually develop malware and spyware (software for tapping data), namely hacktivist (activist for the particular purpose which operates in a way to penetrate the tissue that becomes the target of their campaign), cybercriminals and nation. Flame is not designed to steal money from bank accounts. The virus is also another of the devices commonly used hacktivist hackers.
So with these two possibilities aside, the only "suspect" is a third party. Moreover, the target of a number of countries in the Middle East and the complexity of the threats that emerged showed that no country or government sponsor research into making this program.
Iran cyber security institutions in English-language site stating Flame has similarities with Stuxnet, the many cyber weapons as an example the first time revealed to the public. It also had the Flame might be associated with the incidence of loss of large amounts of data on the number of Iran's computer networks.
Composer: John Gitoyo S Pd.
Sources:
- http://www.securelist.com/en/blog/208193522/The_Flame_Questions_and_Answers , May 28, 2012, 13:00 UTC.
- http://en.wikipedia.org/wiki/Flame_ (malware) , June 1, 2012 at 21:56 UTC.
- http://www.solopos.com/ , Wednesday, May 30, 2012.

Tidak ada komentar:
Posting Komentar